Single Sign-On
If your question is not addressed below, contact us through our support form and we will get back to you shortly.
Single Sign-on (SSO) is a one-credential solution for signing into multiple applications. You can set up SSO with the identity provider (IdP) of your choice and enable users to access Remote Desktop using the IdP credentials, without another password to manage. It encourages stronger passwords and allows better credential management.
Note: Remote Desktop Admin will not be able to sign in using SSO.
To set up SSO, you need to configure your identity provider and then configure your Remote Desktop account. Admin can configure SSO for users and enable their access to Remote Desktop by signing in to a central identity provider.
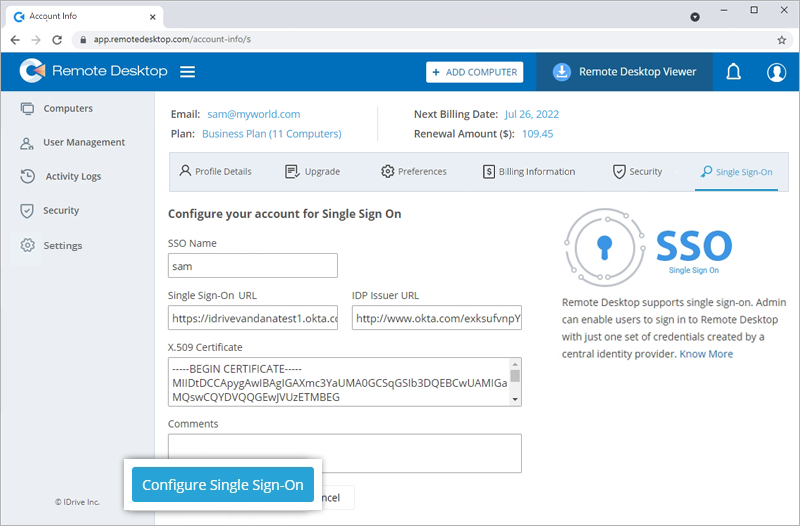
To configure SSO for your Remote Desktop account,
- Sign in to Remote Desktop via any browser.
- Navigate to 'My Account' > 'Single Sign-On'.
- Enter a name for your SSO profile.
- Enter the URLs and add the X.509 certificate received from your IdP.
Note: X.509 certificate should only be in .pem or .cer format. - Click 'Configure Single Sign-On'.
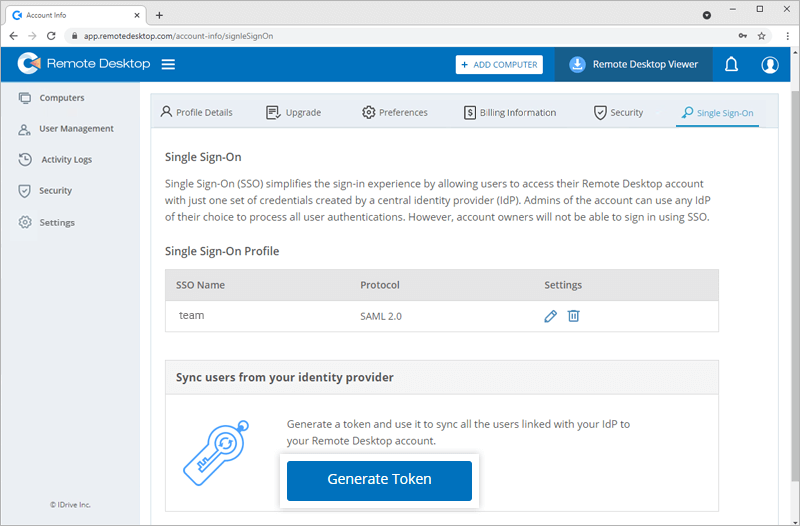
To generate a token for syncing contacts,
- Sign in to Remote Desktop via any browser.
- Click the profile displayed on the top-right corner and click 'My Account'.
- Navigate to 'Single Sign-On' > 'Sync users from your identity provider' and click 'Generate Token'. A token will be generated.
- Click 'Copy Token' to copy and save it for future reference.
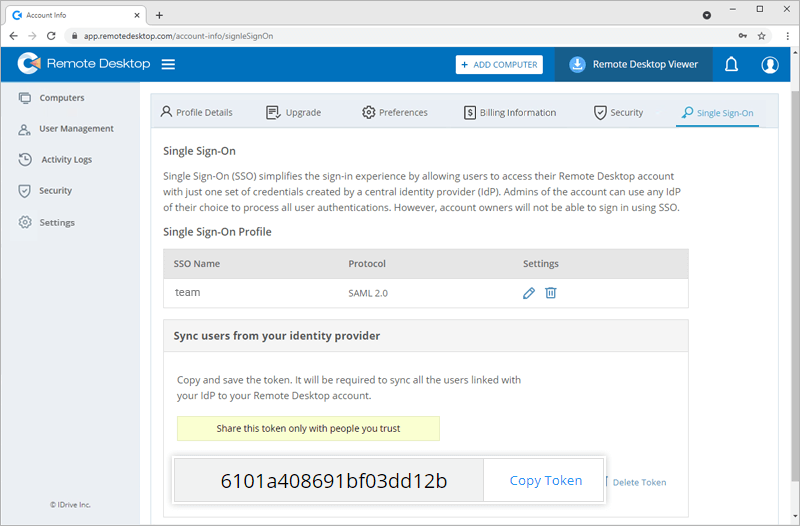
- Use the token to sync contacts from Okta, OneLogin, and Azure AD.
You can either select SSO for sign-in while inviting users to create an account or enable SSO for existing users.
To invite SSO users,
- Sign in to Remote Desktop via any browser.
- Go to the 'User Management' tab and click 'Add User'.
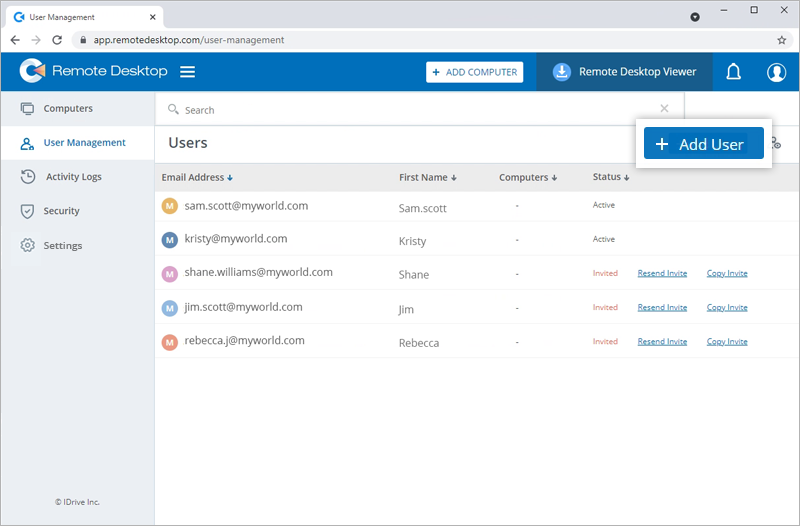
- Enter the user email address in the 'Email Address' field.
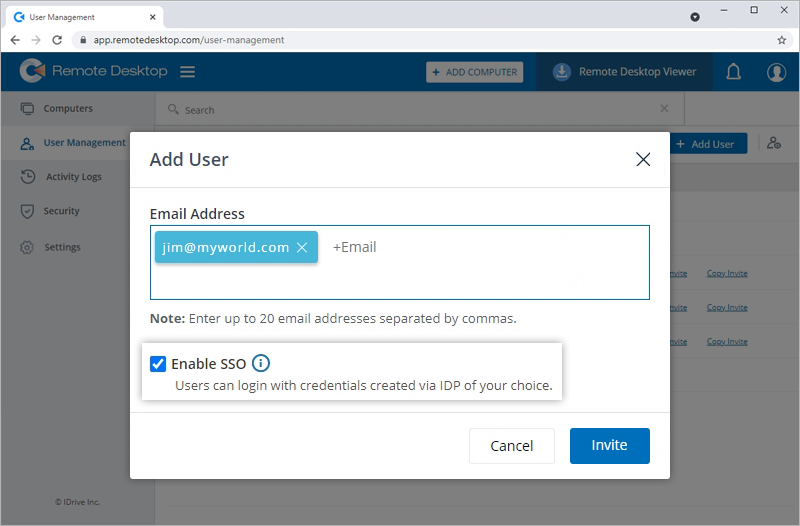
- Tick the 'Enable SSO' checkbox.
Note: If you select the checkbox, users won't have to set a password for their account. - Click 'Invite'.
To enable SSO for existing users,
- Sign in to Remote Desktop via any browser and go to the 'User Management' tab.
- Hover on the user you want to edit and click
 .
. - Select 'Enable SSO'.
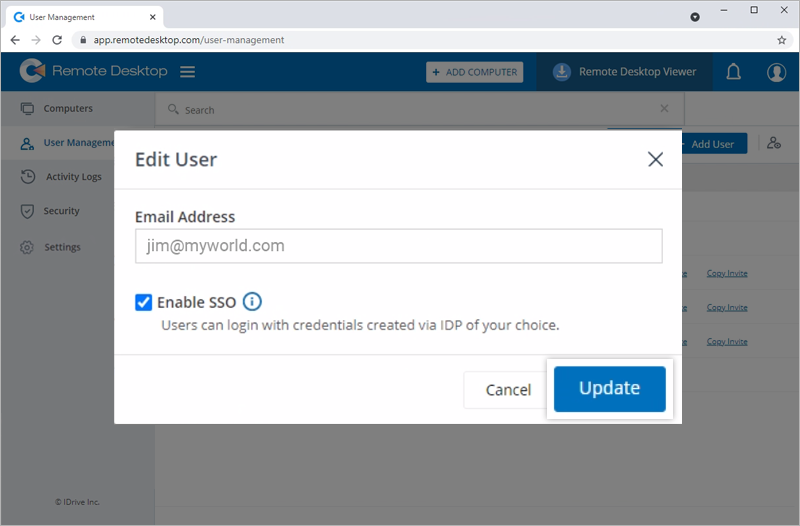
- Click 'Update'.
To edit an SSO profile,
- Sign in to Remote Desktop via any browser.
- Navigate to 'My Account' > 'Single Sign-On'.
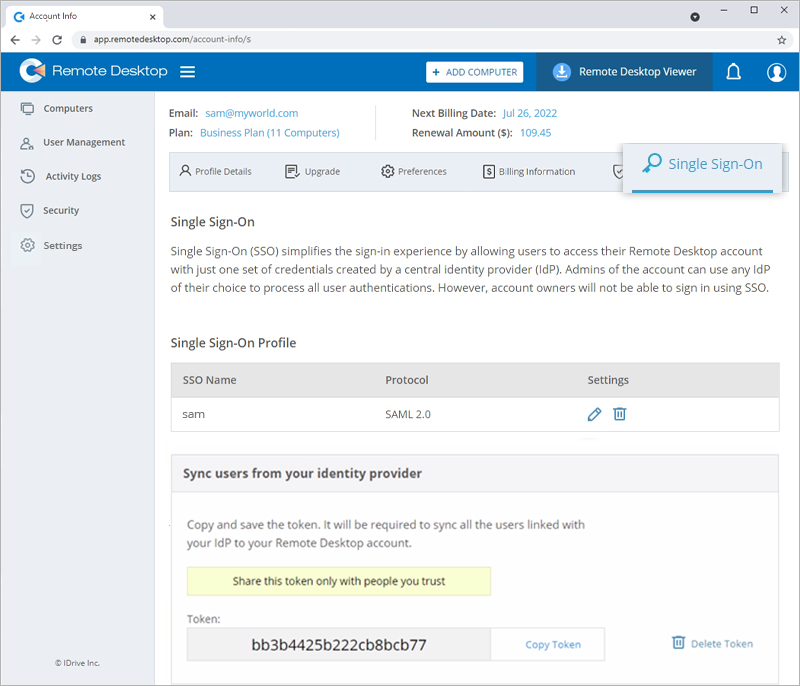
- Click
 corresponding to the SSO profile you wish to edit.
corresponding to the SSO profile you wish to edit.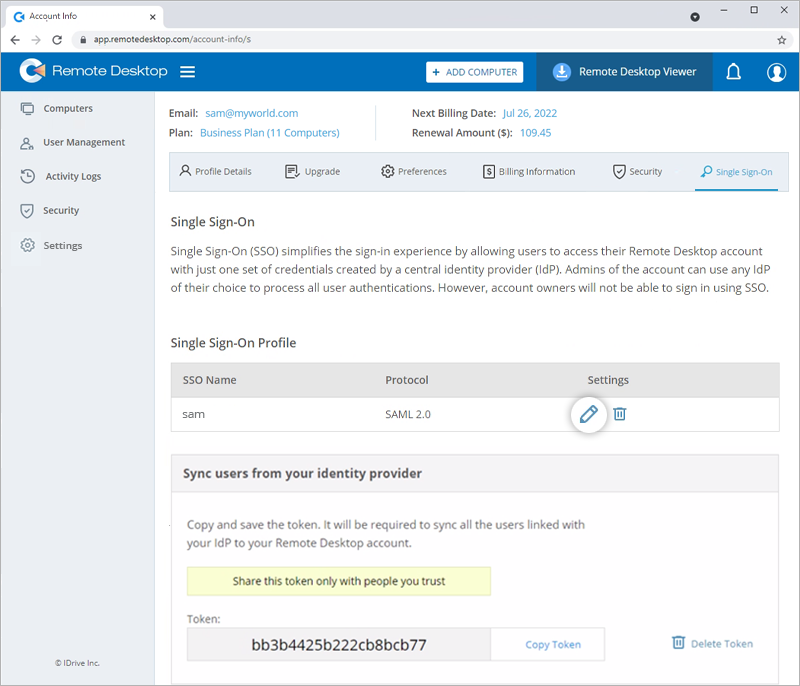
- Edit as per your requirement and click 'Update Single Sign-On'.
Note: You can edit the SSO name, Single Sign-On URL, IDP issuer URL, and X.509 Certificate, and add comments.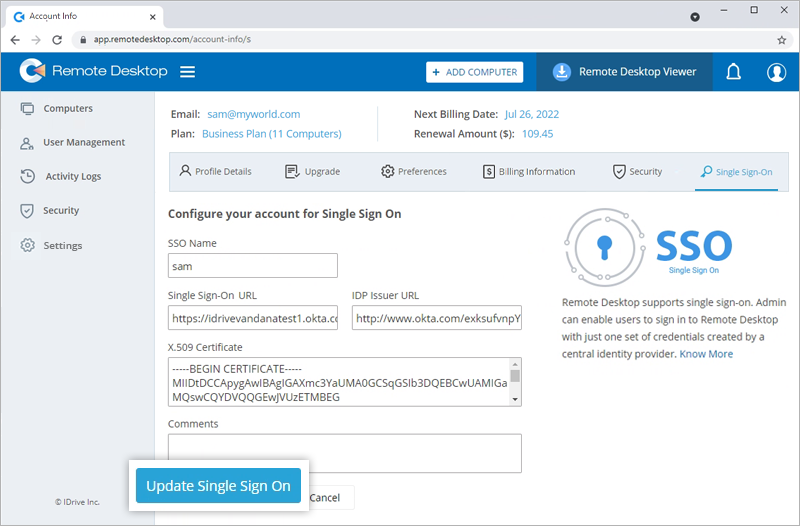
The SSO profile will be updated.
Yes, you can remove an SSO profile from your account.
To remove an SSO profile,
- Sign in to Remote Desktop via any browser.
- Navigate to 'My Account' > 'Single Sign-On'.
- Click
 corresponding to the SSO profile you wish to delete.
corresponding to the SSO profile you wish to delete.
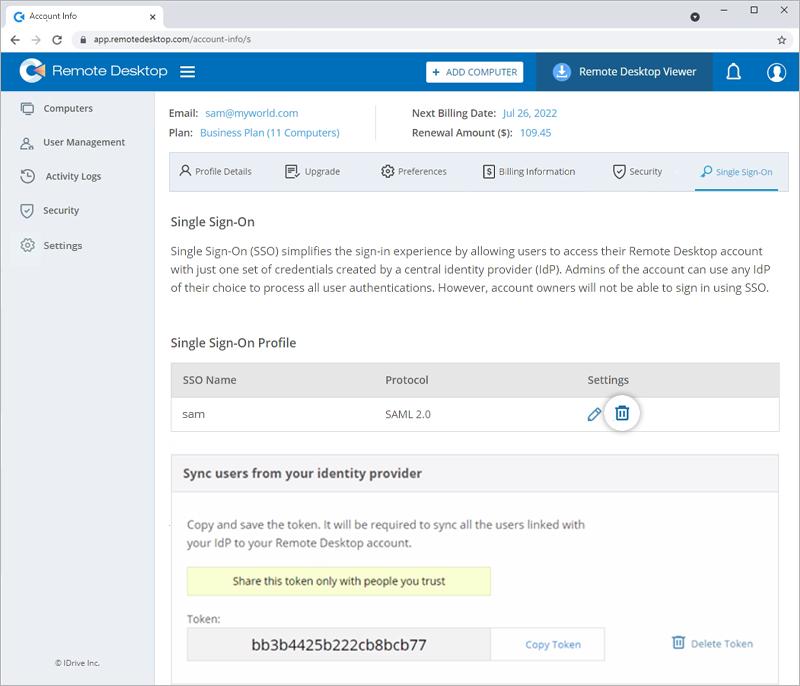
- Click 'Delete' in the confirmation popup to remove the SSO profile.
Deleting the SSO profile will remove Single Sign-On for all users linked with this profile and they will have to use their registered email and password for sign-in.
Remote Desktop supports sign-in via credentials created using Standard Assertion Markup Language (SAML) 2.0. SAML URLs and certificate is needed for implementing SAML authentication, which can be obtained from any supported IdP.
Once you register with an IdP of your choice, you will receive the following:
- IdP Issuer URL: This URL uniquely identifies the application for which the Single Sign-On is being configured.
- Single Sign-On URL: This URL processes an authentication request from the user's browser and returns an authentication response to verify the user.
- X.509 certificate (Base64): An X.509 certificate is a security certificate that you receive from your identity provider to verify your identity. It comes in different formats, but Remote Desktop only accepts .pem or .cer format.
To sign in to the Remote Desktop account via SSO, a user needs to,
- Click 'Single Sign-On (SSO)' on the sign-in screen.
- Enter 'Email Address' and click 'Sign in'. The user will be redirected to the IdP web sign-in page.
- Enter the username and password registered with the IdP, when prompted to enter credentials. On successful validation of user identity, the user will be redirected to the Remote Desktop account.